Its time to connect to our Secure Operations Cloud..
An unlimited number and variety of assets
Stealth Connect brings an additional set of eyes to the behavior of your assets.
As Stealth Connect ingests more data, it will start to predict the future behavior of the asset.
Stealth Connect notifies you in real-time of important events

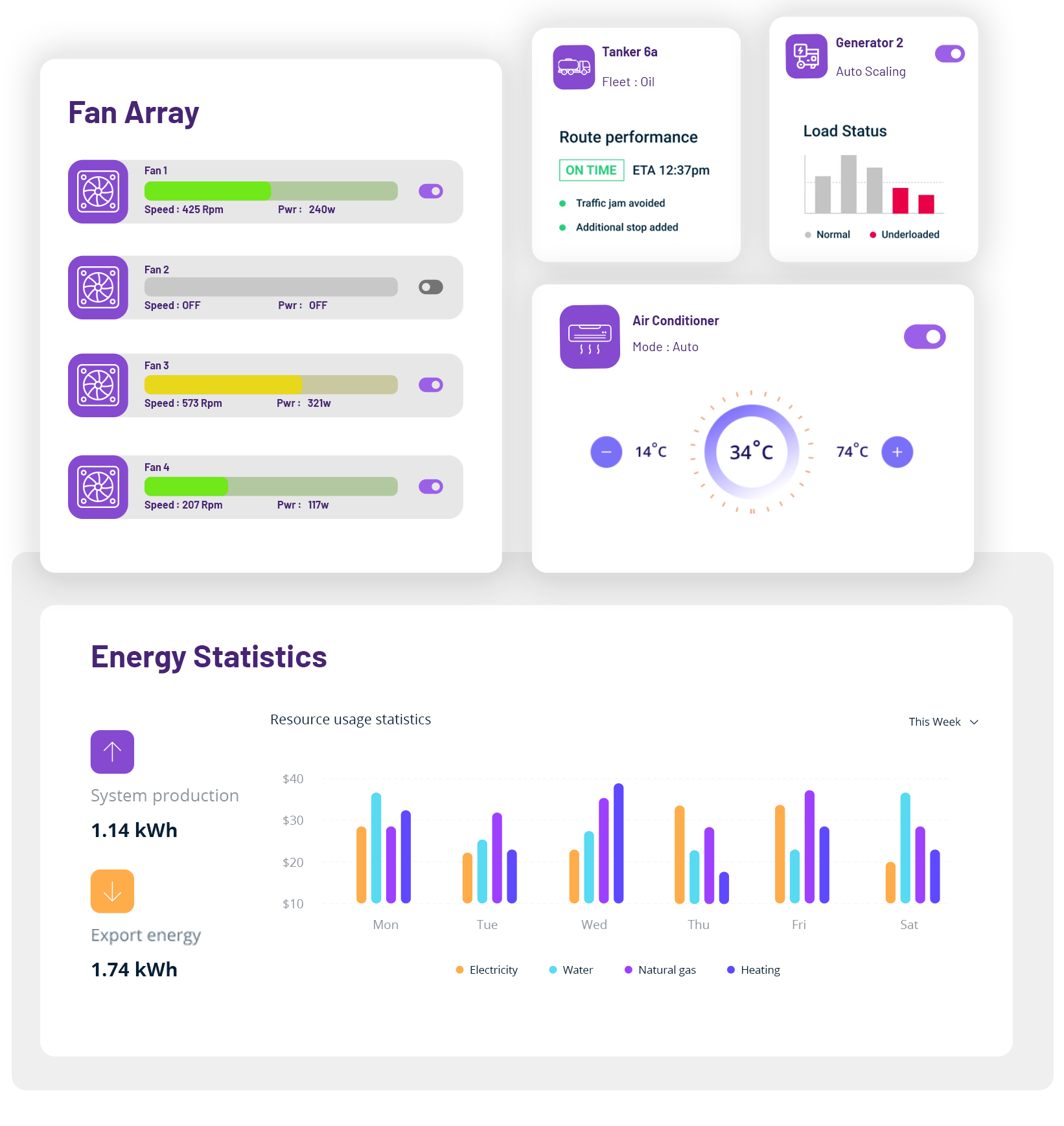

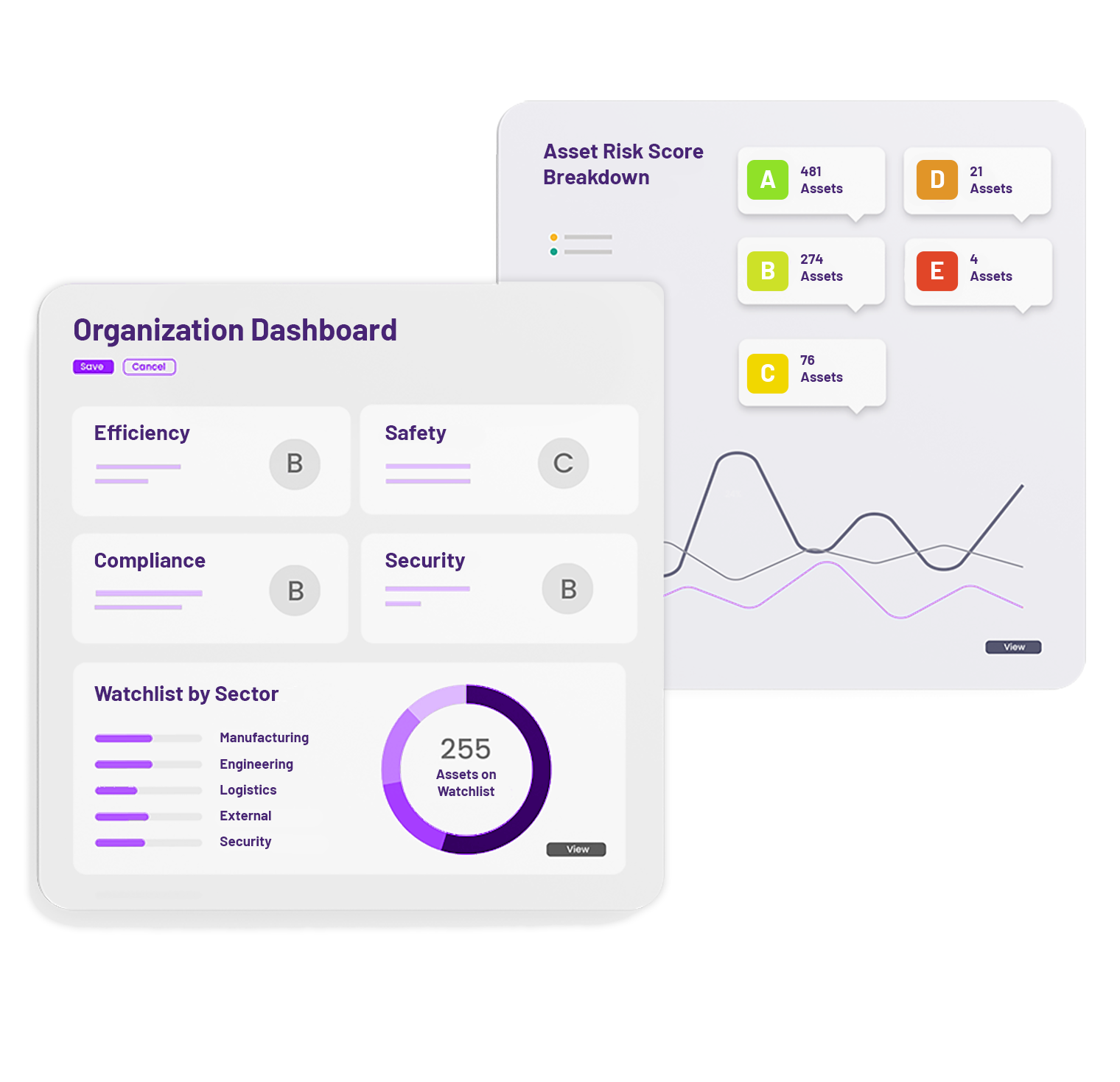

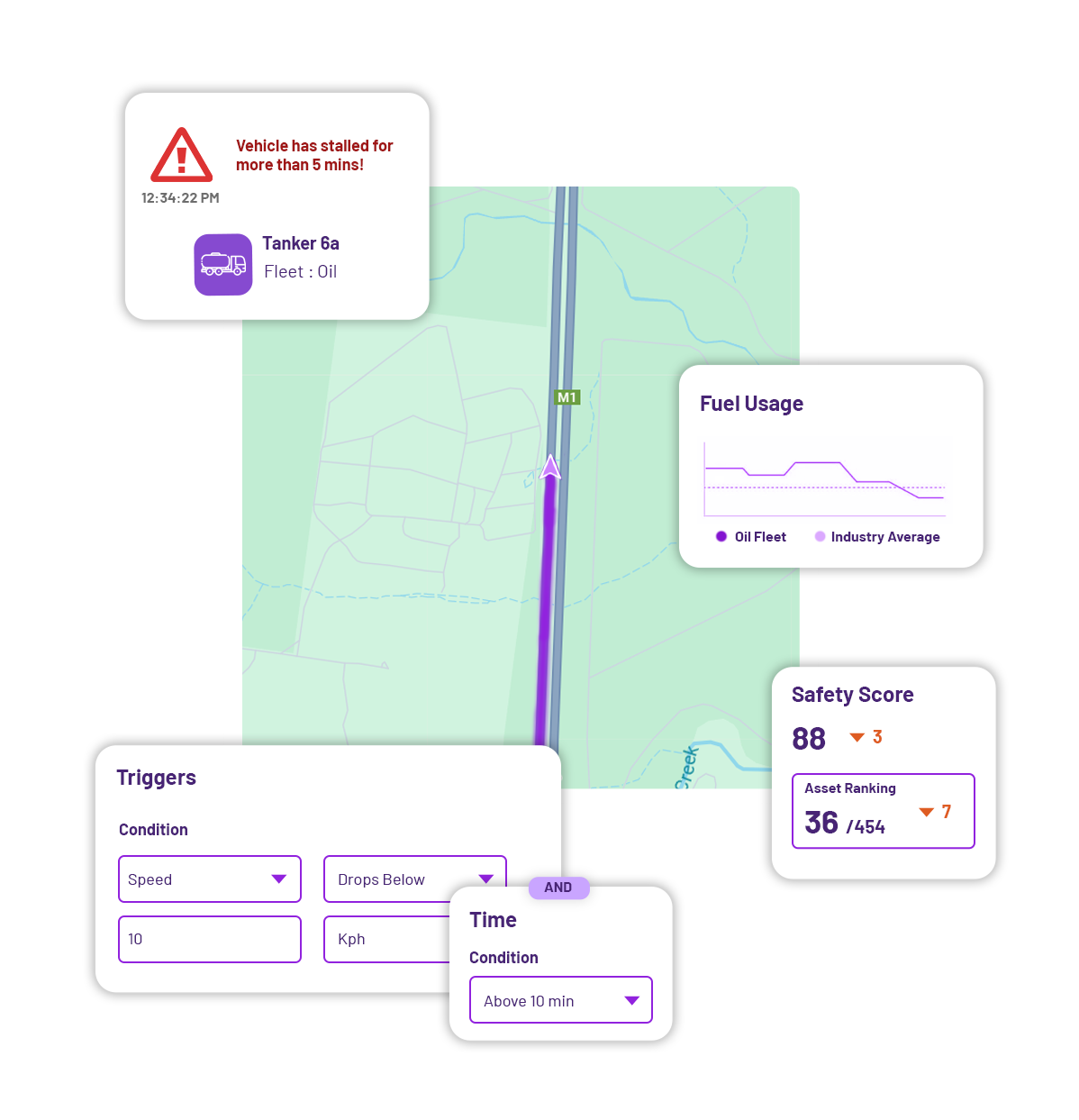







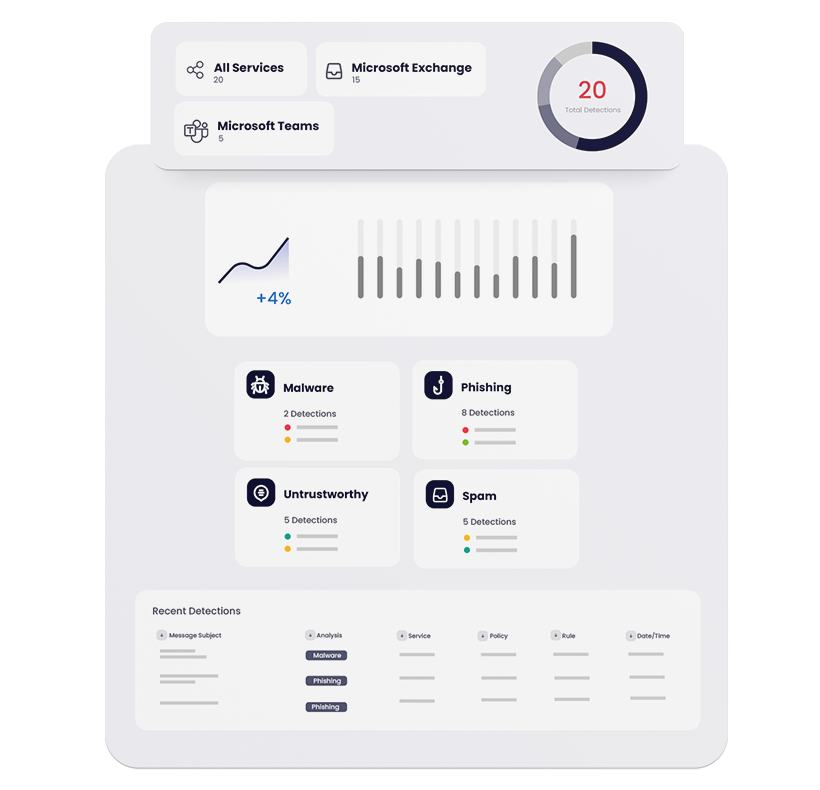
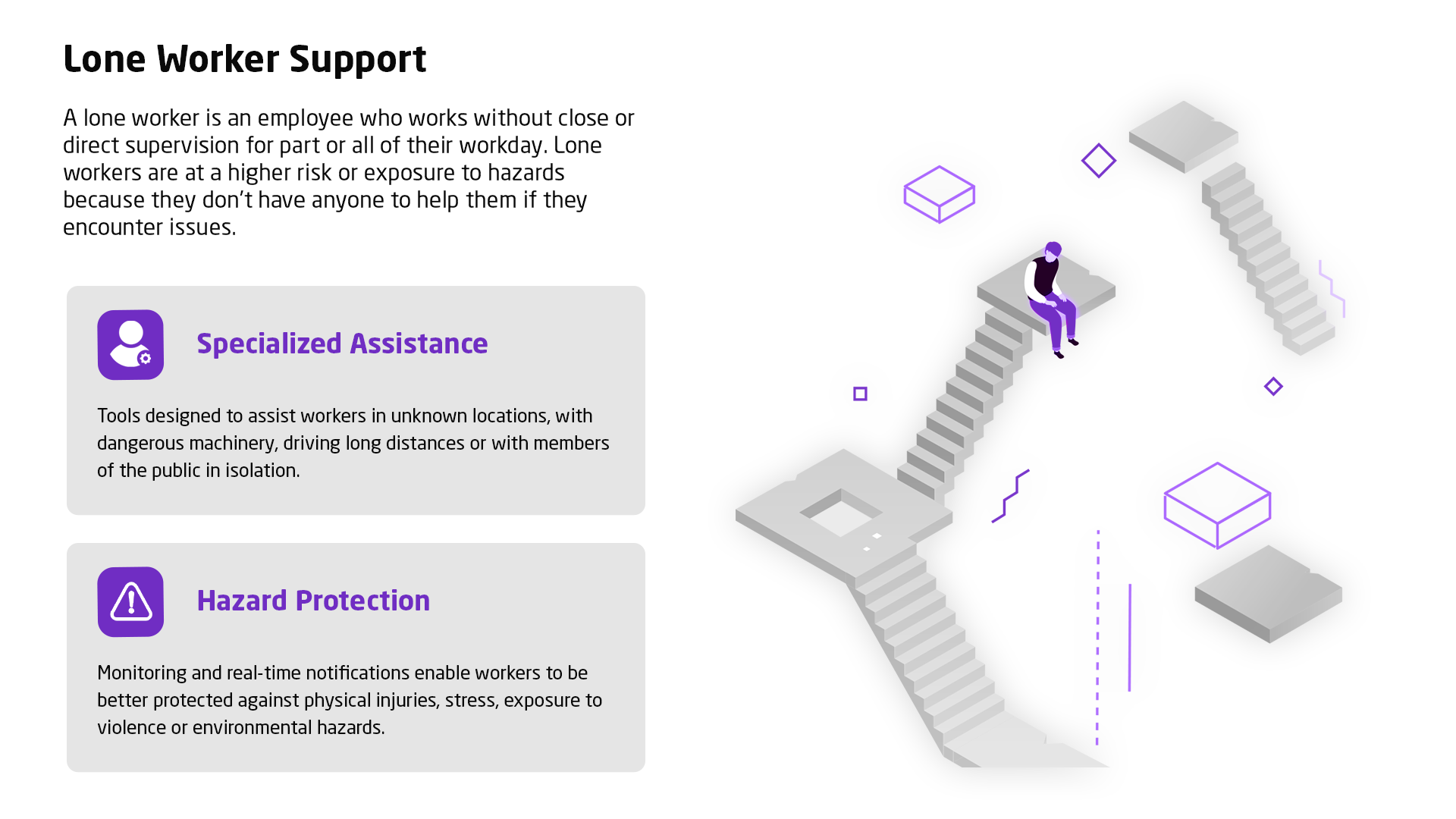
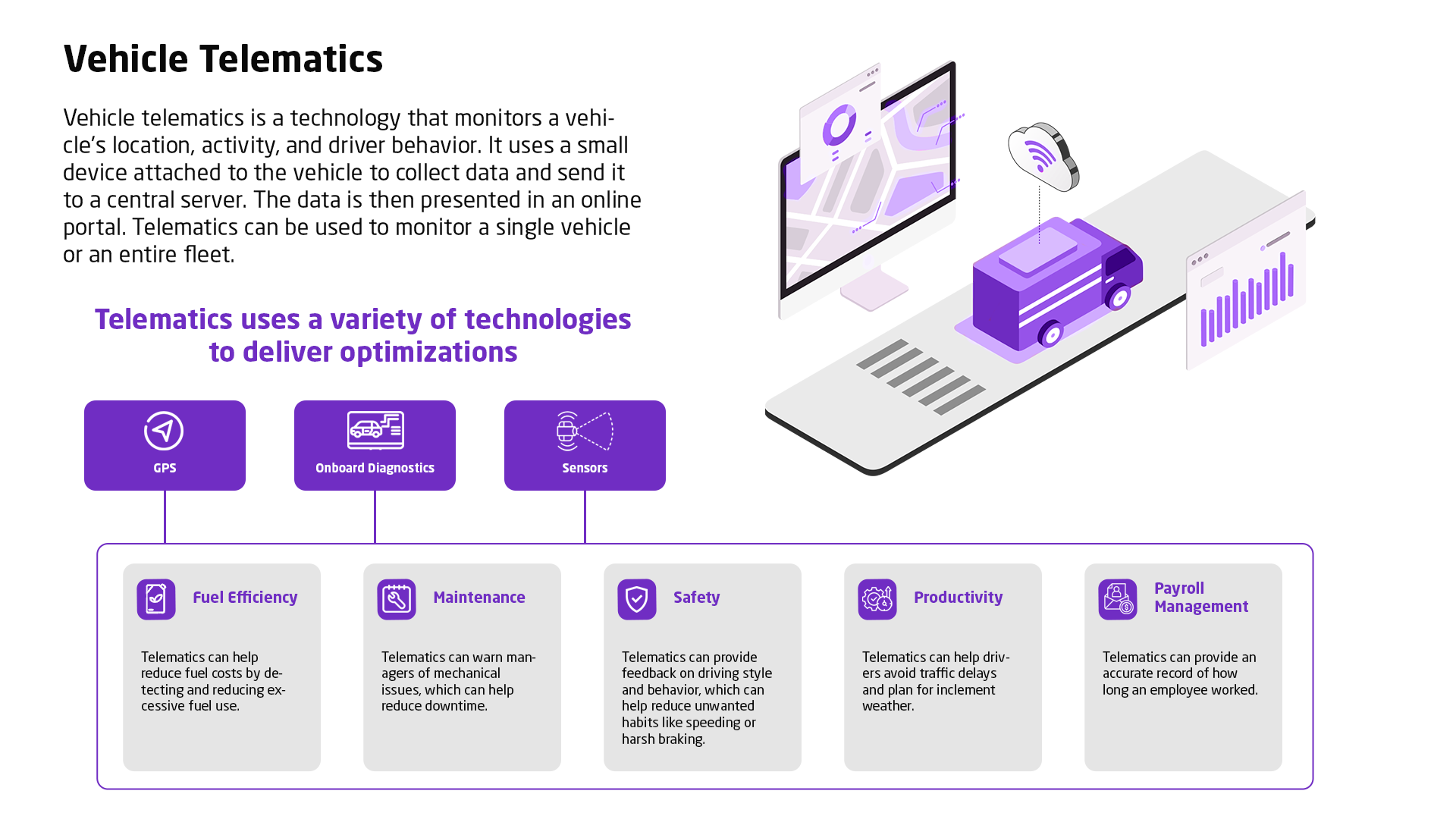
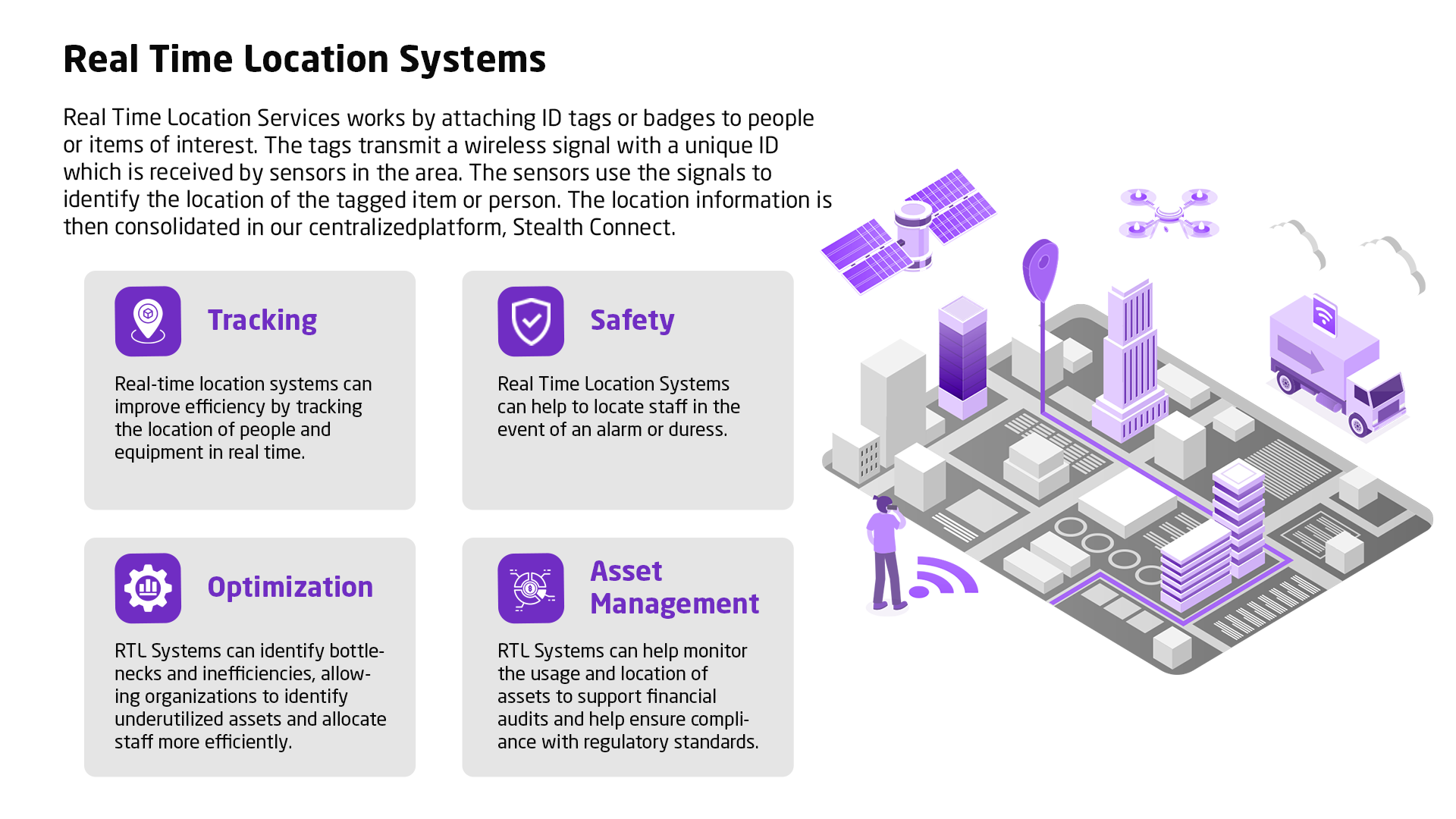
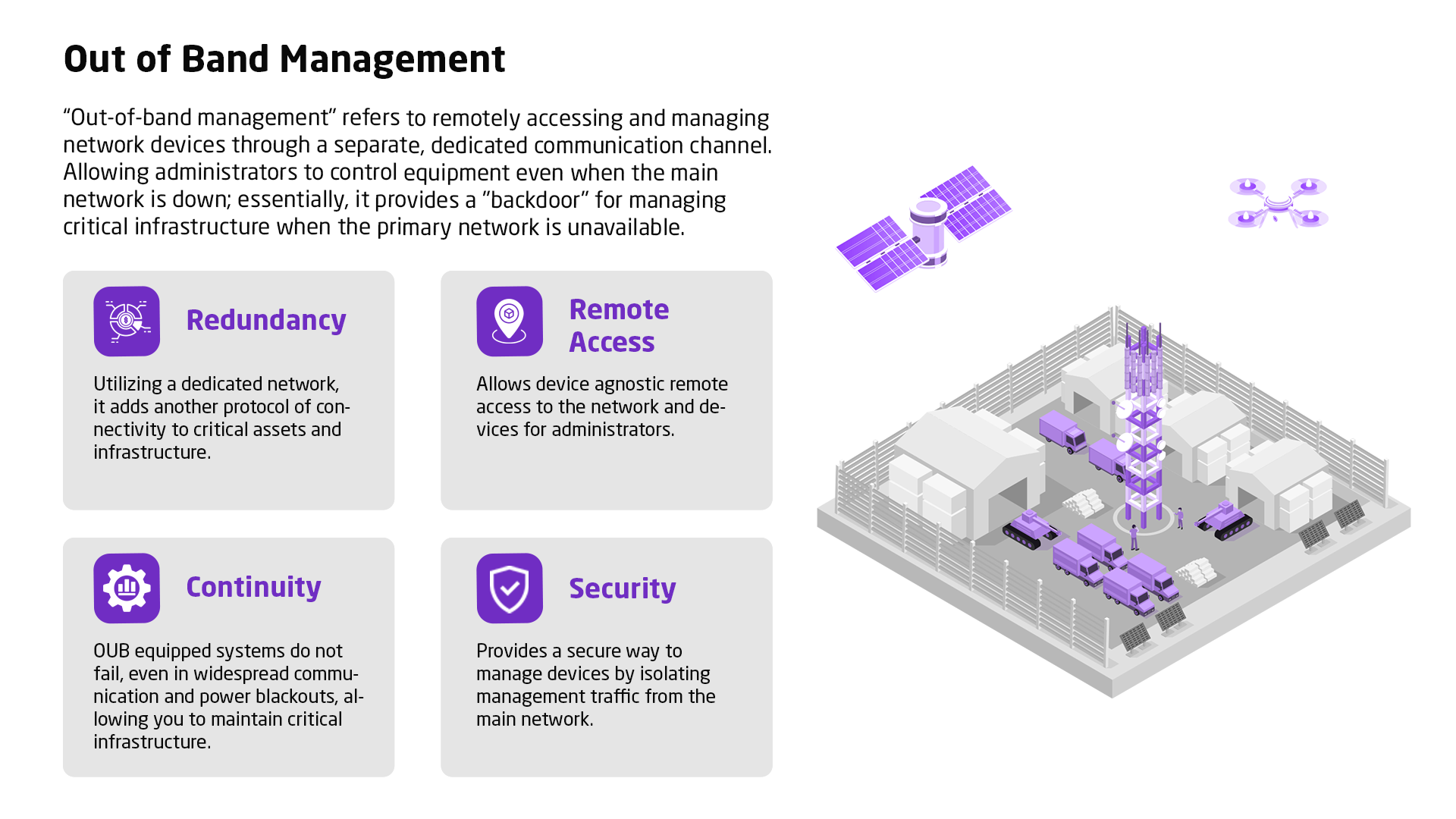
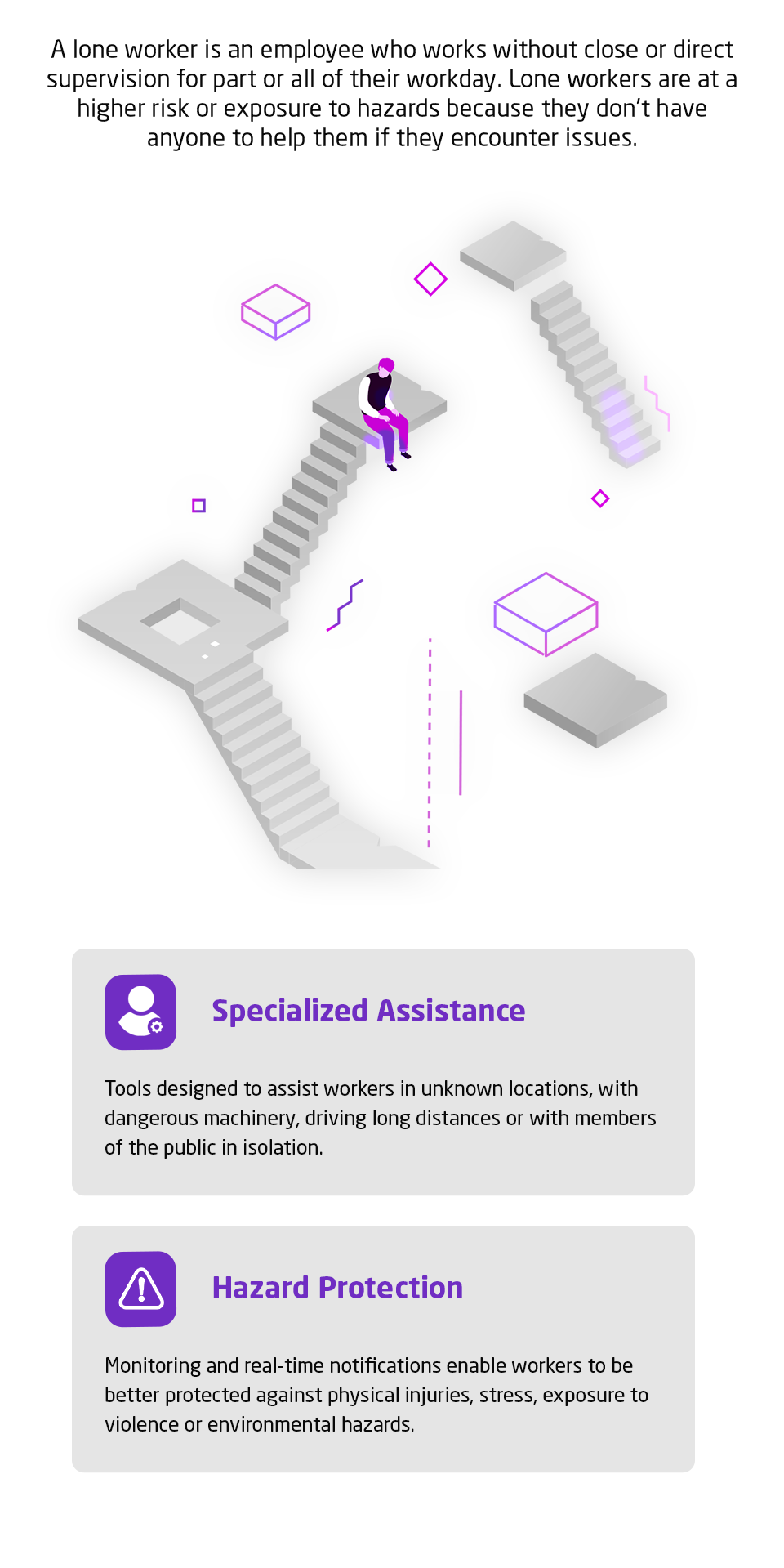
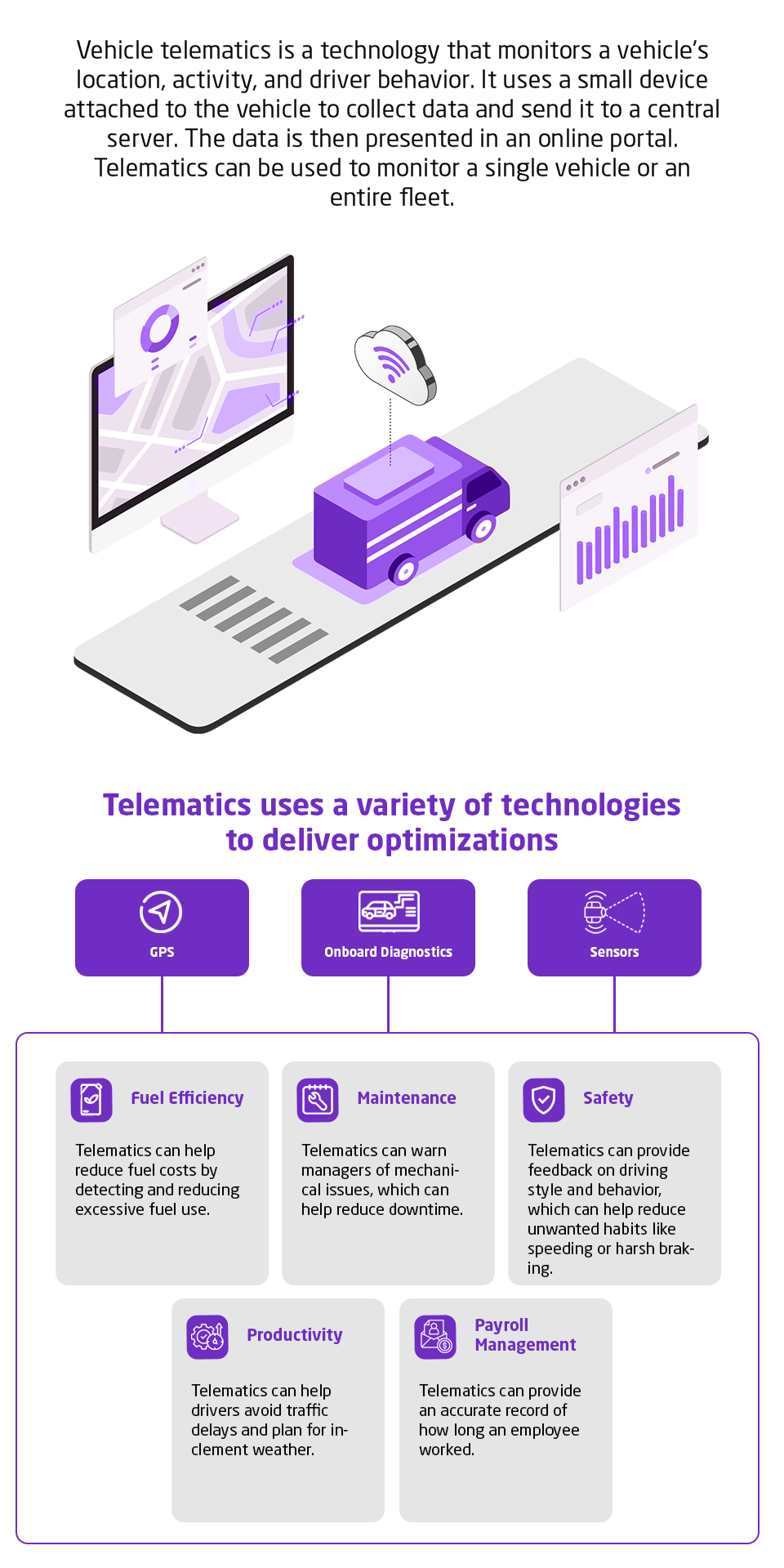
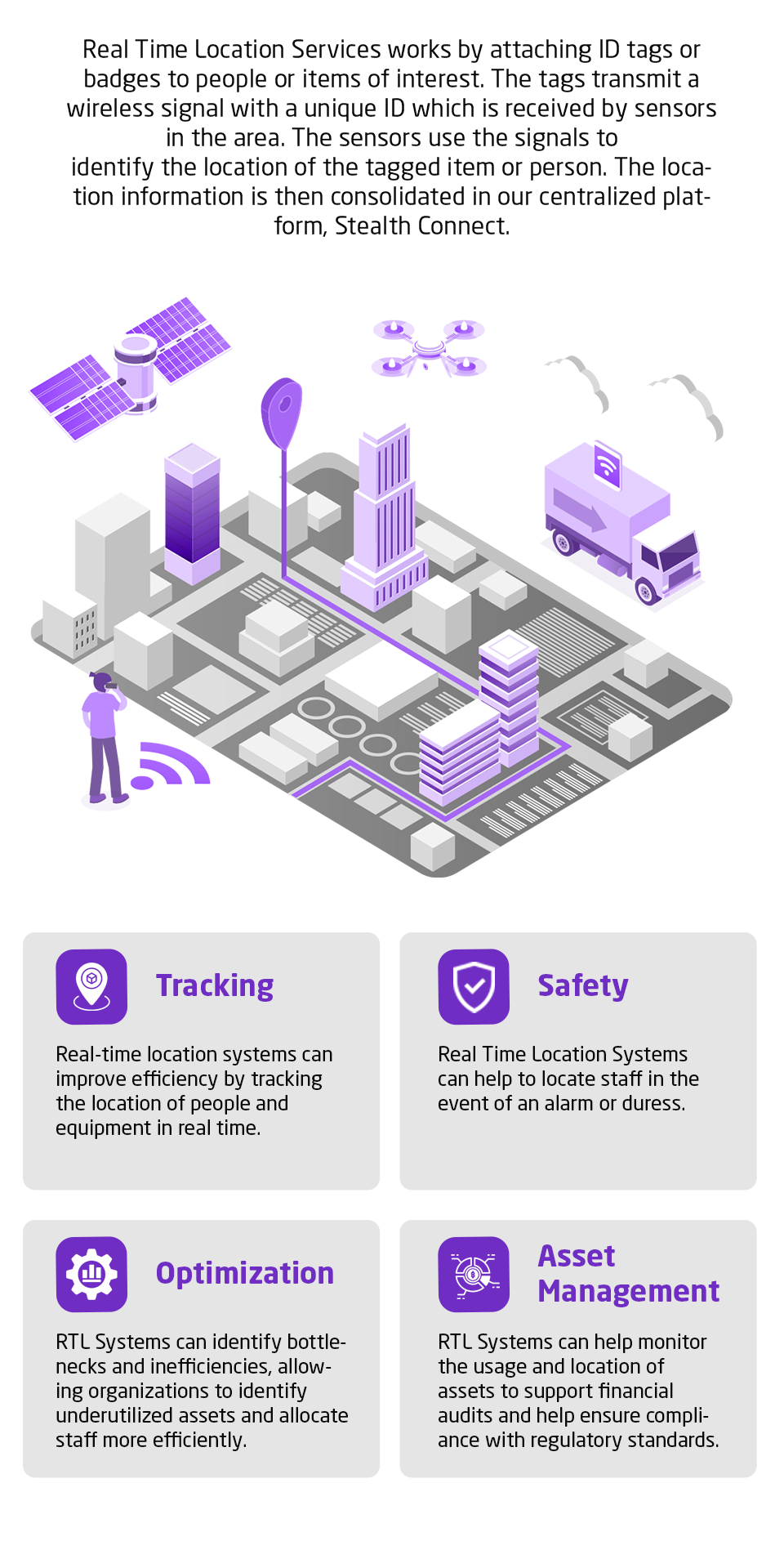
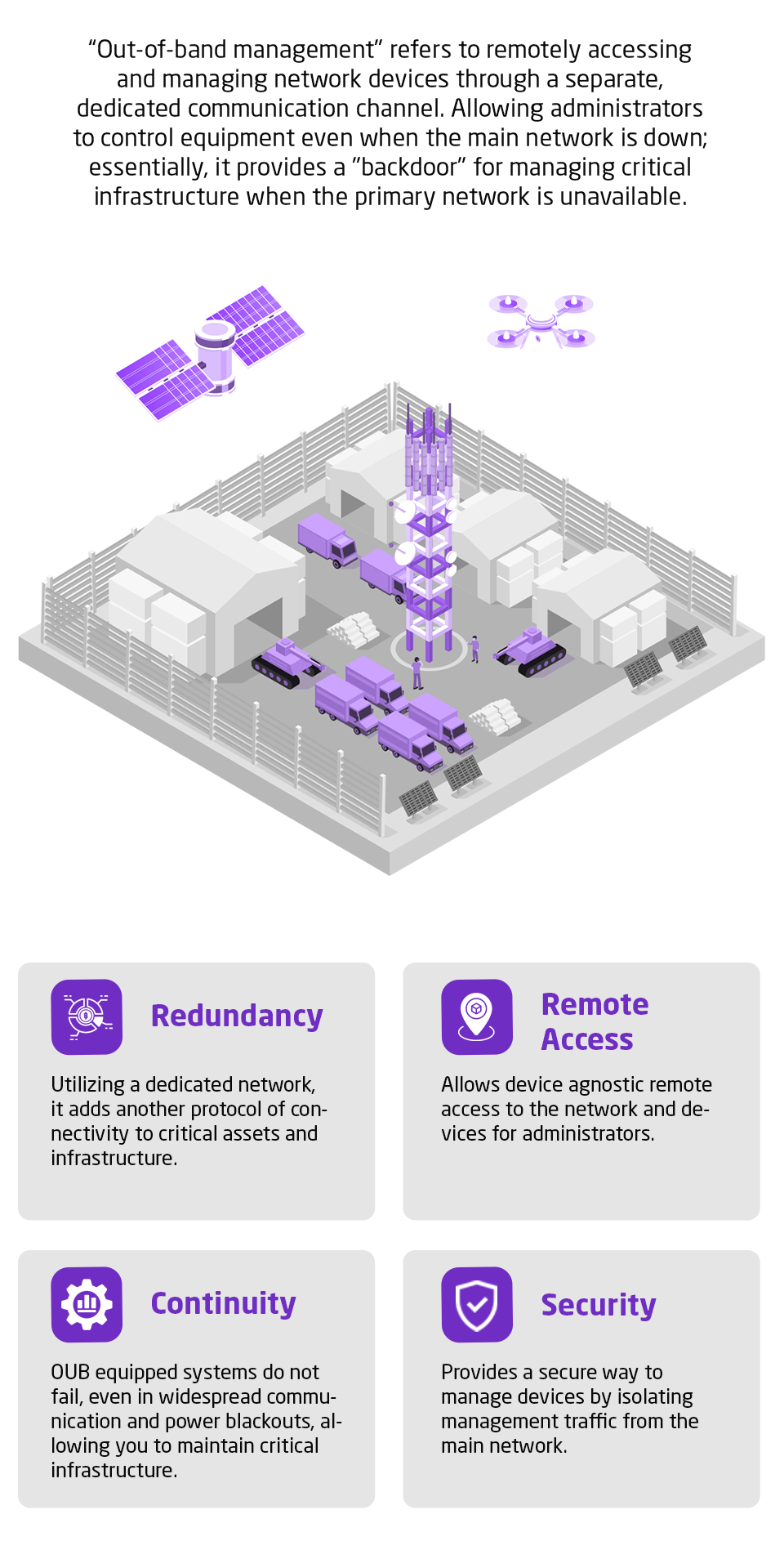
Current asset management methodology is outdated, individual asset risk visibility is poor and policy making is detached from a cyber security strategy.
We provide you with a customized integrated and efficient platform that lets you instantly visualize, prioritize and communicate real-time risk across all your assets.
All of our Partners are carefully selected, our goal is to harden your security posture and assist you in building your Best of Integration “Cyber Fortress”. Relationships are key @ TOM SHAW, and we are nothing without them..
We empower our customers to move new controls in and out and hand the ultimate management and control to you the customer..
Evaluate and learn how the platform can help your business..
Please enter your details below and we will be in touch shortly.