ASV v's Pen Testing - Know your Risk
Security professionals are continually searching for their real cybersecurity gaps amongst the overload of vulnerability data.
With IT infrastructure and cyber threats evolving faster, it is critically important that real vulnerabilities are treated before they are exploited. While penetration testing services may pinpoint such threats accurately, these services cannot scale in scope or be applied in a continuous manner.
Penetration testing involves ethical hackers simulating attacks against a company’s security infrastructure to identify exploitable vulnerabilities. It is commonly conducted annually for each endpoint at a cost of up to $40 000 per test. Most pen tests typically cover only 15% of IT assets and up to 40% of scanner alarms are false positives. As a result, we as security professionals, have come to accept assumptions as the norm given the inaccurate, stale, and context-lacking data in our vulnerability management systems.
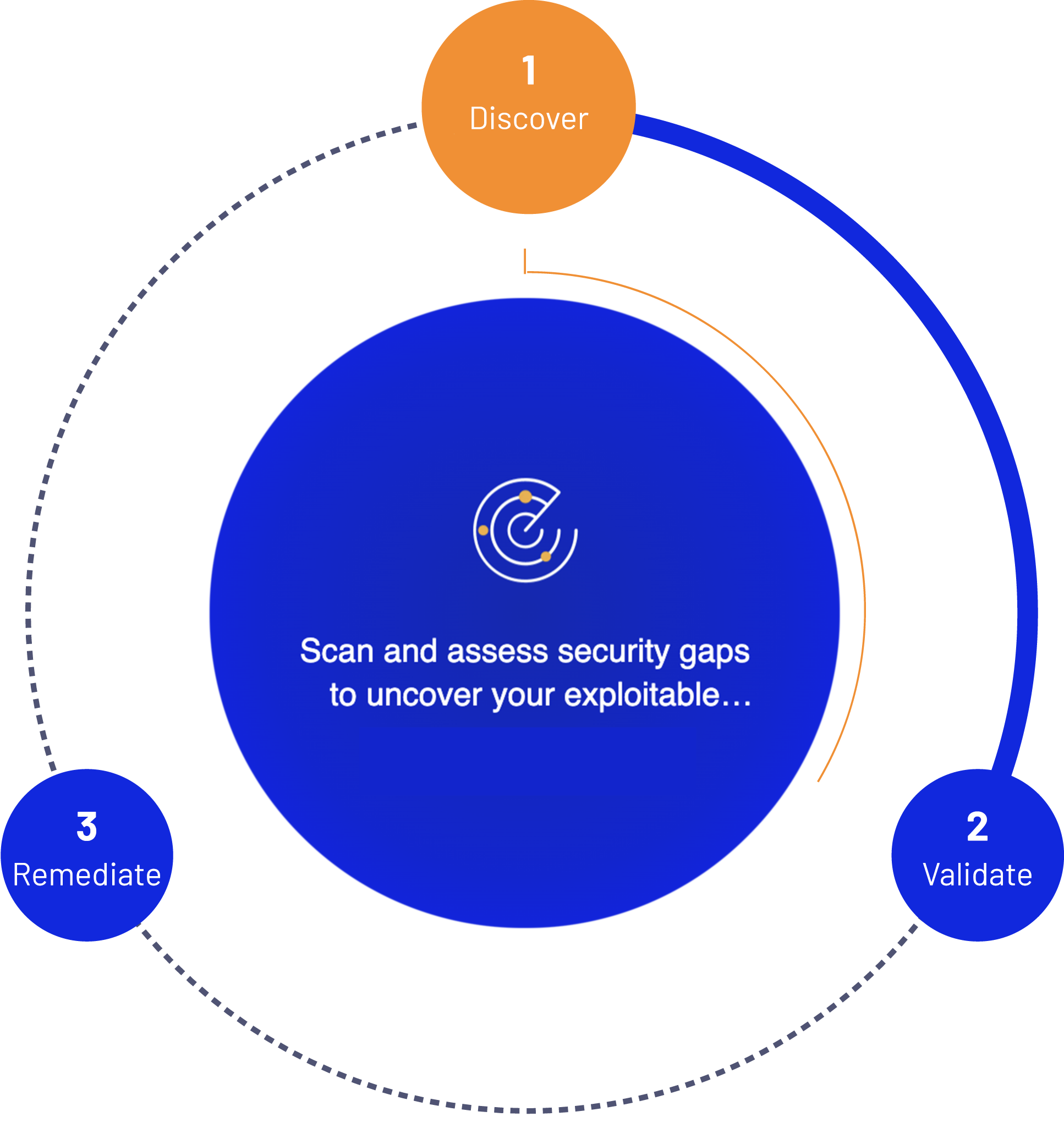
True knowledge of our exposure enables us to focus our resources on fixing the real security gaps. This is achieved by Automated Security Validation. Being a software construct that leverages orchestration and automation, it independently tests and validates security controls (automatically) as often as needed, where the volume of tests conducted is not the billable factor, as opposed to a cost per iteration from a pen testing group . It is complete, accurate, and provides a risk-based remediation roadmap by continuously emulating real-life attacks and validating the efficacy of defensive controls in real time.
ASV focusses first on remediating the breachable and risk-bearing weaknesses that are most attractive to the threat landscape and their actors as they are created, so that security readiness is validated before anything malicious transpires.
The validation-remediation cycle is accelerated, third party reliance and expense is reduced, and security professionals can more efficiently focus only on security gaps proven to be a potential breach-point.
The old world of Pen Testing is outdated. Automated Security Validation now allows security professionals to shift from reactively operating under assumptions to proactively making decisions based on accurate, real time data. ASV enables you to know your risk and your breach’ability.
Wayne Shaw CEO and Founder TOM SHAW
With IT infrastructure and cyber threats evolving faster, it is critically important that real vulnerabilities are treated before they are exploited. While penetration testing services may pinpoint such threats accurately, these services cannot scale in scope or be applied in a continuous manner.
Penetration testing involves ethical hackers simulating attacks against a company’s security infrastructure to identify exploitable vulnerabilities. It is commonly conducted annually for each endpoint at a cost of up to $40 000 per test. Most pen tests typically cover only 15% of IT assets and up to 40% of scanner alarms are false positives. As a result, we as security professionals, have come to accept assumptions as the norm given the inaccurate, stale, and context-lacking data in our vulnerability management systems.
True knowledge of our exposure enables us to focus our resources on fixing the real security gaps. This is achieved by Automated Security Validation. Being a software construct that leverages orchestration and automation, it independently tests and validates security controls (automatically) as often as needed, where the volume of tests conducted is not the billable factor, as opposed to a cost per iteration from a pen testing group . It is complete, accurate, and provides a risk-based remediation roadmap by continuously emulating real-life attacks and validating the efficacy of defensive controls in real time.
ASV focusses first on remediating the breachable and risk-bearing weaknesses that are most attractive to the threat landscape and their actors as they are created, so that security readiness is validated before anything malicious transpires.
The validation-remediation cycle is accelerated, third party reliance and expense is reduced, and security professionals can more efficiently focus only on security gaps proven to be a potential breach-point.
The old world of Pen Testing is outdated. Automated Security Validation now allows security professionals to shift from reactively operating under assumptions to proactively making decisions based on accurate, real time data. ASV enables you to know your risk and your breach’ability.
Wayne Shaw CEO and Founder TOM SHAW